How to configure 802.1X via ISE 2.4.
- What is 802.1X used for? 802.1X is used for secure network authentication. If you are an organization dealing with valuable and sensitive information, you need a secure method of transporting data. 802.1X is used so devices can communicate securely with access points (enterprise-grade routers).
- The IEEE 802.1X standard defines how to provide authentication for devices trying to connect with other devices on LANs or wireless LANs. But to understand it and why you should care means.
What you'll learn in this course
The Introduction to 802.1X Operations for Cisco Security Professionals (802.1X) v2.0 shows you how to configure and prepare to deploy Cisco® Identity-Based Networking Services (IBNS) solutions based on Cisco Identity Services Engine (ISE), Cisco Catalyst switches, and Cisco Wireless LAN Controllers. You will learn the fundamentals of the 802.1X protocol and configuration, Cisco IBNS, configuring access for non-supplicant devices, Cisco ISE deployment options, architectural components, considerations with 802.1X, and more. You will also gain hands-on experience configuring 802.1X–based network services using the Cisco Identity Services Engine and a Cisco Catalyst switch.
Course duration
- E-learning: Equivalent of 2 days of instruction with videos, practice, and challenges
How you'll benefit
This class will help you:
- Learn about and practice configuring Cisco Identity-Based Networking Services solutions at your own pace
- Build your skills using Cisco Identity-Based Networking Services (IBNS) to secure network connectivity and resources
802.1x Is Concerned With
Who should enroll
- Security architects
- Design engineers
- Network engineers
- Cisco integrators and partners
How to enroll
- For e-learning, visit the Cisco Learning Network Store.
- For digital library access, visit Cisco Platinum Learning Library.
- For e-learning volume discounts, email ask_cpll@cisco.com.
Technology areas
- Networking
- Security
What Is 802.1x Authentication

Update 10/1/2018 – Check out my latest post Part 5 below. You may be able to skip all of the other stuff!!
The Links first so you don't have to scroll so far. These are also on the menu at top for easy access. Since I ended up with so much content for this topic, I felt that it warranted a landing page. Hopefully you will be able to easily navigate through these topics and find some useful nuggets to save yourself some headaches down the road.
Part 1 – Building an 802.1x Computer Authentication Script
Part 2 – Building an 802.1x Enabled WinPE Boot Image
Part 3 – Integrating 802.1x Authentication into a Bare Metal Task Sequence
Part 4 – Integrating 802.1x Authentication into an In-Place Upgrade Task Sequence
Part 5 – Dynamic Whitelisting using the Cisco ISE External RESTful Service
Bonus – Tips and Tricks
How to hack winrar password using cmd. If find yourself on this page, you have either 1) made a wrong turn and ended up here by mistake or 2) are tasked with getting IEEE 802.1x Authentication to play nice with your Windows Operating System Deployment. If its option 1, save yourself! Go look for some cat videos or something. You don't want to be here, trust me! If its option 2, welcome to the club. Come on in and make yourself comfortable, it's gonna be a long ride. For my team, this has been one of the most frustrating things to work with/around in our environment. My goal with this series (Yes, this is going to take a few sheets of paper) is to share what I've learned over the past few years and the discoveries I've made. I'm using ConfigMgr/SCCM with Cisco ISE providing our 802.1x protection, so all of the following is geared toward SCCM Task Sequences and the integration between the Windows ADK, WinPE, Wired AutoConfig, Windows 10 and 802.1x. Oh, and Cisco ISE.
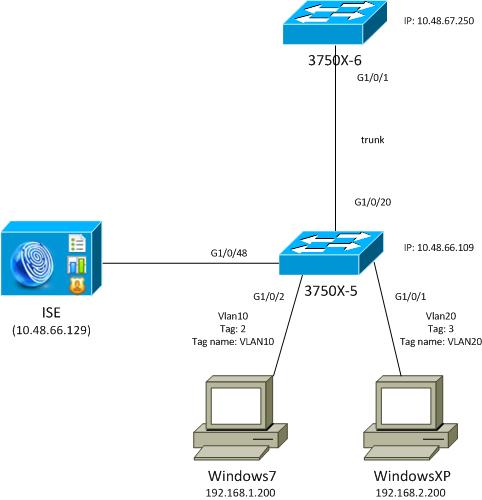
There are multiple ways to configure your network interface for 802.1x authentication and the options you choose will depend on how your 802.1x protection service is configured. For my environment, Cisco ISE will accept either valid domain user credentials or a valid machine certificate. For several years, we used a script to import an 802.1x user authentication profile along with a service account and password to configure authentication on the LAN interface. We soon realized that we would have to update our WinPE Boot Image every 3 months since we are required to reset passwords every 3 months. This is a hassle that we wanted to do away with. So, I developed the solutions that follow to help us switch from user authentication to computer authentication.
802.1x Is A Great Example Of
Now, you may be asking why we would do this and not just build machines in a secure build room. I'm so glad you asked. Because we hate ourselves and wanted to make things difficult!! Honestly, we've done that for quite some time and it has worked pretty well. As we are moving from Windows 7 to Windows 10 with an eye on Modern Management and Windows AutoPilot, we wanted to move to a user-driven imaging/upgrade model. A user can initiate an upgrade from their desk and minimize the manpower required to support the effort.

- What is 802.1X used for? 802.1X is used for secure network authentication. If you are an organization dealing with valuable and sensitive information, you need a secure method of transporting data. 802.1X is used so devices can communicate securely with access points (enterprise-grade routers).
- The IEEE 802.1X standard defines how to provide authentication for devices trying to connect with other devices on LANs or wireless LANs. But to understand it and why you should care means.
What you'll learn in this course
The Introduction to 802.1X Operations for Cisco Security Professionals (802.1X) v2.0 shows you how to configure and prepare to deploy Cisco® Identity-Based Networking Services (IBNS) solutions based on Cisco Identity Services Engine (ISE), Cisco Catalyst switches, and Cisco Wireless LAN Controllers. You will learn the fundamentals of the 802.1X protocol and configuration, Cisco IBNS, configuring access for non-supplicant devices, Cisco ISE deployment options, architectural components, considerations with 802.1X, and more. You will also gain hands-on experience configuring 802.1X–based network services using the Cisco Identity Services Engine and a Cisco Catalyst switch.
Course duration
- E-learning: Equivalent of 2 days of instruction with videos, practice, and challenges
How you'll benefit
This class will help you:
- Learn about and practice configuring Cisco Identity-Based Networking Services solutions at your own pace
- Build your skills using Cisco Identity-Based Networking Services (IBNS) to secure network connectivity and resources
802.1x Is Concerned With
Who should enroll
- Security architects
- Design engineers
- Network engineers
- Cisco integrators and partners
How to enroll
- For e-learning, visit the Cisco Learning Network Store.
- For digital library access, visit Cisco Platinum Learning Library.
- For e-learning volume discounts, email ask_cpll@cisco.com.
Technology areas
- Networking
- Security
What Is 802.1x Authentication
Update 10/1/2018 – Check out my latest post Part 5 below. You may be able to skip all of the other stuff!!
The Links first so you don't have to scroll so far. These are also on the menu at top for easy access. Since I ended up with so much content for this topic, I felt that it warranted a landing page. Hopefully you will be able to easily navigate through these topics and find some useful nuggets to save yourself some headaches down the road.
Part 1 – Building an 802.1x Computer Authentication Script
Part 2 – Building an 802.1x Enabled WinPE Boot Image
Part 3 – Integrating 802.1x Authentication into a Bare Metal Task Sequence
Part 4 – Integrating 802.1x Authentication into an In-Place Upgrade Task Sequence
Part 5 – Dynamic Whitelisting using the Cisco ISE External RESTful Service
Bonus – Tips and Tricks
How to hack winrar password using cmd. If find yourself on this page, you have either 1) made a wrong turn and ended up here by mistake or 2) are tasked with getting IEEE 802.1x Authentication to play nice with your Windows Operating System Deployment. If its option 1, save yourself! Go look for some cat videos or something. You don't want to be here, trust me! If its option 2, welcome to the club. Come on in and make yourself comfortable, it's gonna be a long ride. For my team, this has been one of the most frustrating things to work with/around in our environment. My goal with this series (Yes, this is going to take a few sheets of paper) is to share what I've learned over the past few years and the discoveries I've made. I'm using ConfigMgr/SCCM with Cisco ISE providing our 802.1x protection, so all of the following is geared toward SCCM Task Sequences and the integration between the Windows ADK, WinPE, Wired AutoConfig, Windows 10 and 802.1x. Oh, and Cisco ISE.
There are multiple ways to configure your network interface for 802.1x authentication and the options you choose will depend on how your 802.1x protection service is configured. For my environment, Cisco ISE will accept either valid domain user credentials or a valid machine certificate. For several years, we used a script to import an 802.1x user authentication profile along with a service account and password to configure authentication on the LAN interface. We soon realized that we would have to update our WinPE Boot Image every 3 months since we are required to reset passwords every 3 months. This is a hassle that we wanted to do away with. So, I developed the solutions that follow to help us switch from user authentication to computer authentication.
802.1x Is A Great Example Of
Now, you may be asking why we would do this and not just build machines in a secure build room. I'm so glad you asked. Because we hate ourselves and wanted to make things difficult!! Honestly, we've done that for quite some time and it has worked pretty well. As we are moving from Windows 7 to Windows 10 with an eye on Modern Management and Windows AutoPilot, we wanted to move to a user-driven imaging/upgrade model. A user can initiate an upgrade from their desk and minimize the manpower required to support the effort.
If you want more info about what 802.1x Authentication is or how to implement it, you won't find that here. I just won't come close to explaining it properly, so if you want to know more, I'm sure someone smarter than me has already geeked-out writing a nice article about the wonders of 802.1x authentication and why it's the most amazing security protocol and such. I just want to know how to get around it so I can get machines imaged and out the door!
